👨🔧 OpenVulnScan Admin Guide Installation 1. Clone the Repository git clone https://github.com/sud...
Tribal Knowledge for the outsider

👨🔧 OpenVulnScan Admin Guide Installation 1. Clone the Repository git clone https://github.com/sud...
🧑💻OpenVulnScan User Guide Introduction OpenVulnScan is a powerful, open-source vulnerability mana...
In an era where open-source tools increasingly shift towards commercial models, the need for accessi...
In a world where software is eating the world, vulnerabilities are multiplying just as fast. Securit...
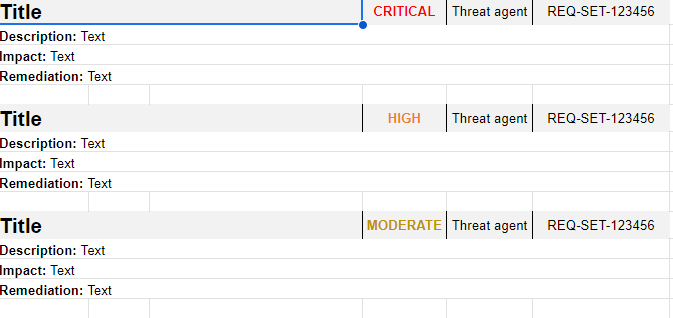
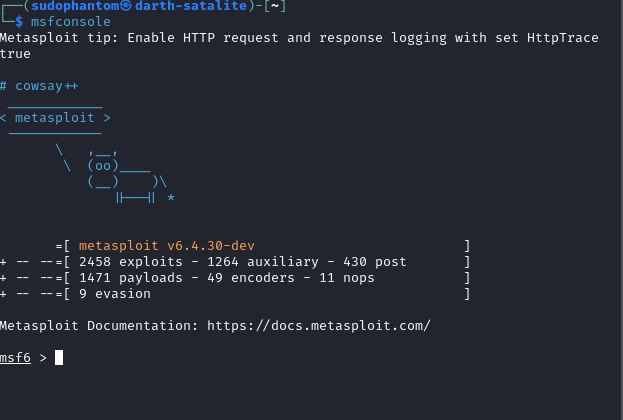
The Exploitation Phase of a Penetration Test
In the ever-evolving landscape of cybersecurity, understanding how to identify vulnerabilities is cr...
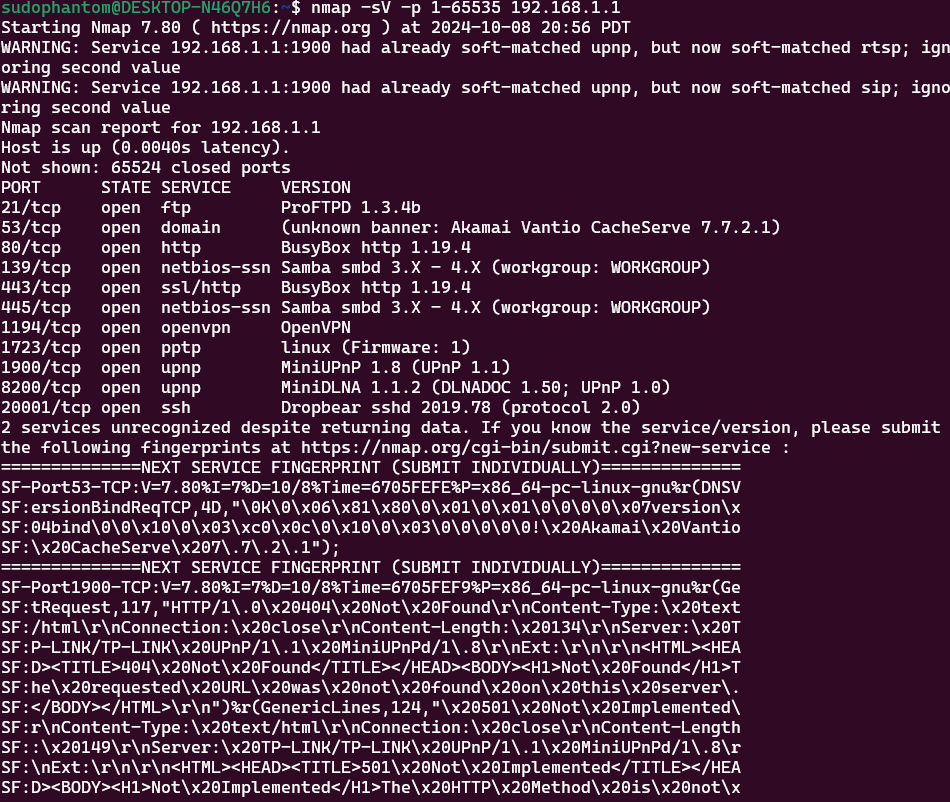
What is Service Enumeration? Service Enumeration is the phase of a penetration test where the tester...