In an era where open-source tools increasingly shift towards commercial models, the need for...
🔍 Introducing OpenVulnScan & VulnChain: An Open and Incentivized Approach to Vulnerability Management
In a world where software is eating the world, vulnerabilities are multiplying just as fast. Security teams everywhere are stretched thin trying to keep up with identifying, classifying, and remediating vulnerabilities in their environments. Traditional vulnerability management tools are often expensive, closed-source, and disconnected from the growing community of ethical hackers, researchers, and open-source developers. That’s where OpenVulnScan and VulnChain come in.
🧩 What is OpenVulnScan?
OpenVulnScan is a modern, open-source vulnerability management tool designed for security professionals, developers, and DevSecOps teams who want transparency, extensibility, and simplicity.
🔧 Core Features:
-
🖥️ Agent-based Package Reporting: Lightweight agents report installed packages from Linux systems.
-
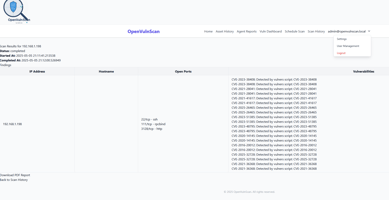
🔎 Nmap-based Unauthenticated Scanning: Automatically scan networked hosts for open ports and known CVEs.
-
📚 Integrated CVE Lookup: Correlates reported packages and scan data with a live CVE database.
-
🔐 OAuth2 & Wallet Authentication: Supports Google/GitHub sign-ins and decentralized wallet-based auth.
-
📊 Dashboard & Reports: View HTML reports of vulnerabilities per agent, system, or package.
-
📡 REST API First: Everything runs on an extensible FastAPI backend for integration or API-first deployments.
It’s designed to be lightweight enough for small teams and powerful enough to integrate into CI/CD pipelines.
🔗 What is VulnChain?
VulnChain builds on the foundation of OpenVulnScan by introducing token-based incentives and blockchain-backed transparency to vulnerability management.
🚀 The Vision:
Think of VulnChain as the “bug bounty meets open vulnerability intel” network. It’s a decentralized network where:
-
Researchers can submit CVE data or package signatures to help the community.
-
Agents can report findings from systems in real-time.
-
Submissions are timestamped, indexed on-chain, and accessible for trustless verification.
-
Contributors are rewarded with tokens for actionable and validated data.
-
Everything is auditable, exportable, and designed for global collaboration.
🛠️ Built With:
-
🪙 Cardano (via Blockfrost) for decentralized storage of report hashes and contributor reputations.
-
📁 IPFS for off-chain storage of vulnerability reports.
-
🔐 JWT / Wallet auth for identifying contributors and reward recipients.
-
📊 OpenVulnScan’s API for real-time data intake.
🌍 Use Cases
| Use Case | Description |
|---|---|
| 🔒 Internal Vulnerability Management | Monitor and manage your own assets with full transparency and no vendor lock-in. |
| 🌐 Threat Intel Collaboration | Share package-level CVE data across organizations without revealing sensitive systems. |
| 🛠️ CI/CD Integration | Use OpenVulnScan’s API to halt builds if critical vulns are detected in newly deployed containers. |
| 💰 Community-Powered Intel | Submit new signatures or exploit proof-of-concepts and earn token rewards on VulnChain. |
| 🏛️ Audit-Ready Reports | Timestamped, signed reports can be exported or verified during compliance audits. |
💡 The Philosophy
We believe that vulnerability intelligence should be open, collaborative, and incentivized — not siloed in overpriced dashboards or limited to closed bug bounty platforms. OpenVulnScan is the free and transparent foundation, and VulnChain is the decentralized community and incentive layer that brings it to life.
Together, they aim to shift security left, not just in development pipelines, but in the global information-sharing lifecycle.
🚧 What’s Next?
-
🌍 OpenVulnScan's hosted demo is coming soon.
-
💻 VulnChain’s initial prototype will launch with Cardano + IPFS testnet support.
-
🔁 Community-driven agents for Windows, macOS, and container environments are in development.
-
📢 We'll be open-sourcing everything — contributions and feedback welcome!
🙌 Join Us
Want to contribute? Deploy an agent? Or just follow along?
📂 GitHub: github.com/sudo-sec/OpenVulnScan
🔗 VulnChain Testnet (coming soon)
💬 Reach out: sudo-sec.xyz/contact
Together, let’s redefine what it means to do vulnerability management — openly, responsibly, and with community at the core.