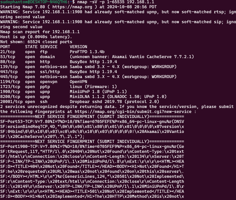
What is Service Enumeration? Service Enumeration is the phase of a penetration test where the...
Searching for Service Exploits
In the ever-evolving landscape of cybersecurity, understanding how to identify vulnerabilities is crucial for both security professionals and ethical hackers. Whether you’re conducting a penetration test or simply looking to improve your system’s defenses, knowing how to leverage tools like Searchsploit, Exploit-DB, Metasploit, and even Google can be invaluable. In this blog post, we’ll explore how to effectively use these resources to find service vulnerabilities.
1. Searchsploit
What is Searchsploit?
Searchsploit is a command-line tool that provides easy access to the Exploit Database from your terminal. It allows you to quickly search for known vulnerabilities based on keywords, CVEs (Common Vulnerabilities and Exposures), or specific software names.
How to Use Searchsploit:
- Install Searchsploit: If you haven’t already, you can install it by cloning the Exploit-DB repository from GitHub.
$ git clone https://gitlab.com/exploit-database/exploitdb $ cd exploitdb |
- Update the Database: Run the update script to ensure you have the latest exploits.
- $ ./searchsploit -u
- Search for Vulnerabilities: Use the search command followed by a keyword related to the service or software you’re investigating. For example:
- $ ./searchsploit apache
-
- Review the Results: The output will show you a list of available exploits, including their paths and descriptions. You can view the details by using:
- $./searchsploit -x <exploit_path>
2. Exploit-DB
What is Exploit-DB? Exploit-DB is a comprehensive database of public exploits and corresponding vulnerable software. It’s an excellent resource for finding detailed information about vulnerabilities, including proof-of-concept code.
How to Use Exploit-DB: 1. Visit the Website: Go to Exploit-DB.
- Search for Exploits: Use the search bar to input relevant keywords, CVEs, or specific service names. You can also filter results by operating system, type of exploit, and date.
- Review the Exploits: Click on an exploit to access detailed information, including the vulnerability description, affected versions, and any available code snippets or links to further resources.
3. Metasploit
What is Metasploit? Metasploit is a powerful penetration testing framework that allows security professionals to find, exploit, and validate vulnerabilities in systems. It integrates with the Exploit-DB and can automate many processes involved in vulnerability testing.
How to Use Metasploit:
- Install Metasploit: If you haven’t already, install Metasploit using the package manager or by following the installation guide on their website.
- Start the Framework:
- > msfconsole
- > msfconsole
- Search for Exploits: Use the search command to find relevant modules. For example, to search for Apache vulnerabilities:
- > search apache
- > search apache
- Select an Exploit: Choose an exploit from the search results and use the
usecommand to load it.- > use exploit/linux/http/apache_druid_js_rce
- > use exploit/linux/http/apache_druid_js_rce
- Configure Options: Set the necessary options, such as target IP and payload.
- > set RHOST <target_ip> set PAYLOAD linux/x86/meterpreter/reverse_tcp
- > set RHOST <target_ip> set PAYLOAD linux/x86/meterpreter/reverse_tcp
- Run the Exploit: Execute the exploit and observe the results.
> exploit
4. Google
Using Google to Find Vulnerabilities Sometimes, a simple Google search can yield valuable information about service vulnerabilities, especially when searching for specific configurations, vulnerabilities, or exploits that may not be widely documented.
How to Use Google for Vulnerability Research:
- Search with Specific Queries: Use advanced search operators to refine your results. For example:
- "CVE-2023-XXXX" site:exploit-db.com
- Combine Keywords: Combine keywords related to the software and vulnerabilities:
- "Apache vulnerability" "exploit"
- Utilize Google Dorks: Use Google Dorks to uncover sensitive information or specific configurations. For example:
- intitle:"index of" "config.php"
- Stay Updated: Follow cybersecurity blogs, forums, and newsletters that report on newly discovered vulnerabilities.

Conclusion
Finding service vulnerabilities is a critical skill in cybersecurity. By leveraging tools like Searchsploit, Exploit-DB, Metasploit, and even Google, you can enhance your ability to identify and address potential security issues. Always remember to conduct your research ethically and responsibly, ensuring you have proper authorization before testing any systems. Happy hunting!